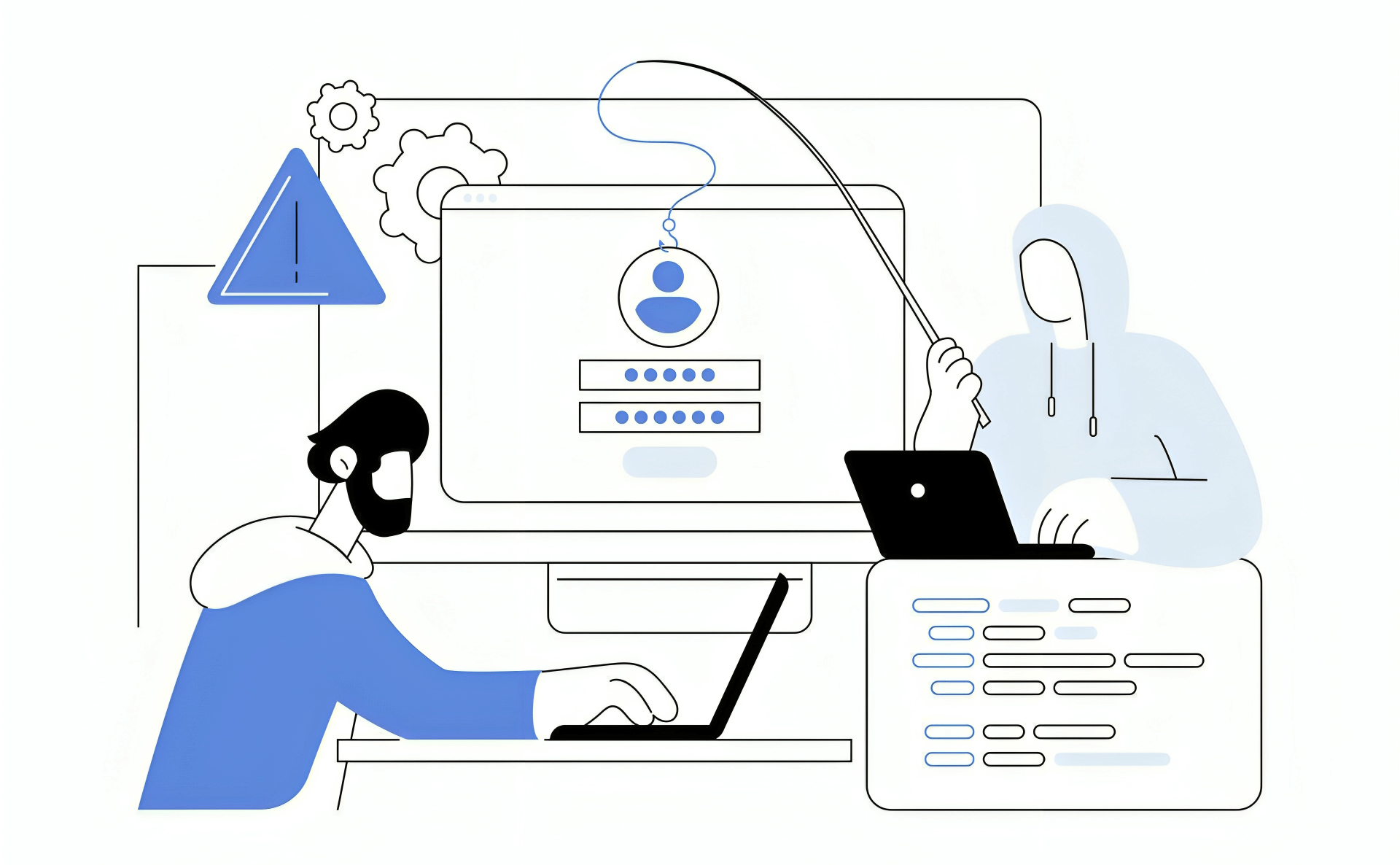
The internet faces an ongoing battle with phishing attacks that compromise user security. This article examines two different approaches to addressing this problem: Clean, readable URLs and Epiarc's human-centric naming system. While both aim to protect users, they take fundamentally different paths with potentially very different security outcomes.
In this article
How phishing attacks exploit URL confusion
Phishing attacks have become one of the most prevalent cybersecurity threats in today's digital landscape. According to recent statistics, 36% of all data breaches in the US are caused by phishing attacks, with organizations losing approximately $17,700 per minute to these scams.1 The problem has grown exponentially, with a 345% increase in unique phishing sites between 2020 and 2021 alone.2

The core vulnerability that phishing exploits is user confusion about URLs. When users receive an email with a link to "securebanklogin.com" instead of their bank's actual domain, many struggle to determine whether it's legitimate. Phishing attacks have evolved to employ sophisticated techniques such as:
- Typosquatting: Creating domains that are slight misspellings of legitimate sites (bankofamerica-secure.com instead of bankofamerica.com)
- URL spoofing: Making the visible link text show one URL while actually linking to another
- IDN homograph attacks: Using Unicode characters that visually resemble Latin letters to create domains that appear identical to legitimate ones
- Subdomain manipulation: Using subdomains to confuse users (login.bank.malicious.com appearing to be from "bank")
The average internet user often fails to properly parse these URLs. Studies show that even when users are aware of phishing risks, they frequently misinterpret domain structures or overlook subtle clues in the URL that would reveal malicious intent. According to CloudFlare's 2023 phishing report, deceptive links account for around 36% of all phishing threats, making them the most common attack vector.3

This fundamental challenge has prompted two distinctly different approaches to addressing the problem.
Clean URLs: Transparency and direct recognition
The clean URL approach advocates for transparency and direct visibility of web addresses. The core principle is straightforward: users should always be able to see exactly what domain they're visiting or about to visit, with browsers designed to highlight the actual domain name rather than obfuscate it.
Clean URLs are characterized by:
- Transparency: The full domain and path structure are visible to users
- Readability: URLs are structured to be human-readable and meaningful
- Simplicity: Avoiding unnecessary parameters, session IDs, or complex paths that confuse users
- Direct recognition: Users can directly evaluate the legitimacy of a site based on its URL
Modern browsers already incorporate features to help users identify legitimate sites, such as highlighting the domain name in the address bar or displaying security indicators for HTTPS connections. Some browsers also implement warning systems for known phishing sites through databases like Google Safe Browsing.
The clean URL approach builds on the existing web infrastructure without adding new layers of abstraction. It doesn't require users to trust third parties to interpret websites for them. Instead, it focuses on education and browser improvements to help users better understand URLs themselves.
For example, an online banking URL might look like:
https://www.firstnationalbank.com/online-bankingWith this approach, users who learn basic URL reading skills can verify that the domain is "firstnationalbank.com" (the legitimate bank domain), the connection is encrypted (https), and the path ("/online-banking") is logical for the service they're accessing.
While not perfect, this system leverages the existing web infrastructure and addresses phishing through transparency rather than abstraction.
Epiarc and similar abstraction approaches: Adding layers of complexity

Epiarc takes a fundamentally different approach to the URL problem. Founded by Alex Greenland (CEO), Dan Cassey (CTO), and Chris Kilding (Director of Research) — the same team behind Epi — Epiarc introduces Archetypal Resource Identifiers (ARIs) — human-centric names that sit as a layer of abstraction above URLs. Instead of showing users technical URLs, the system displays familiar, contextual names.
The core components of the Epiarc system include:
- ARIs (Archetypal Resource Identifiers): Human-friendly names like "Australian Broadcasting Company" instead of "abc.net.au"
- Linkbases: Repositories of ARI-to-URL mappings that users or organizations can create and share
- User Agents: Software that subscribes to linkbases and handles the resolution of ARIs to actual URLs
- Context-dependent naming: The same ARI (e.g., "ABC") might resolve to different websites depending on context (Australian Broadcasting Corporation in Australia vs. American Broadcasting Company globally)
Similar abstraction approaches are being explored elsewhere. For example, the Dia browser is testing a way to displays page titles in the address bar rather than URLs, only showing the actual URL when the user hovers over it. This trend towards URL abstraction is gaining traction, as noted by Josh Miller:
A modern URL bar (in @diabrowser):
— Josh Miller (@joshm) May 15, 2025
• Page Title not "/2025/12/seo-spam" gibberish
• Space on both sides of "/" for readability
• Hover to reveal & edit URL
• Emphasize domain for trust+security
Dia isn't just AI. It's refined browser basics too, @browsercompany style. pic.twitter.com/Fle8qqNeYo
The theoretical benefit is that users can interact with websites through names they naturally understand rather than technical URLs. For instance, instead of remembering "https://www.facebook.com," users could simply type "Facebook" as an ARI. The system would then resolve this to the correct URL based on the linkbases the user has subscribed to.
Proponents argue this is more intuitive for users who don't understand URL structures and could help prevent phishing by allowing people to access sites through trusted names rather than potentially confusing URLs.
The new attack surface: How abstraction creates vulnerabilities
While Epiarc's approach might seem promising on the surface, it introduces several significant security concerns that could potentially make phishing easier rather than harder:
Linkbase manipulation and compromise
The entire security model of Epiarc depends on the integrity of linkbases. If a malicious actor can compromise a linkbase or trick users into subscribing to a fraudulent one, they could map legitimate-sounding ARIs to phishing sites. A compromised linkbase could map "First National Bank" to "malicious-site.com" instead of the actual bank's website. Users would see the familiar "First National Bank" name and have no reason to suspect they're being redirected to a fraudulent site. By the time the actual URL is visible (if ever), the user may have already entered sensitive information. Unlike the direct nature of URLs, users must trust the linkbase providers to maintain accurate and secure mappings. This introduces a new dependency and potentially a single point of failure.
Confusion with similar entity names
The context-dependent nature of ARIs creates significant vulnerabilities when dealing with similarly named entities. Consider how "ABC Bank" could refer to multiple different banking institutions across different regions, "Metro Bank" might be a legitimate bank in multiple countries, each with different websites, and "First Federal Credit Union" could be any of dozens of similarly named financial institutions. Without the specificity of domain names, users would need to rely entirely on context to determine which entity they're actually interacting with. This ambiguity provides fertile ground for phishers to exploit confusion.
Masking critical security indicators
The abstraction approach fundamentally hides important security information that users need to make informed decisions. By hiding the actual URL by default (as seen in the Dia browser example), users lose access to critical information:
- Whether the site uses HTTPS encryption
- Which specific domain they're connecting to
- What country's top-level domain is being used (.us, .co.uk, etc.)
- Whether there are suspicious elements in the URL path or parameters
When users are trained to rely on names rather than URLs, they lose the ability to spot common phishing indicators like suspicious domains or unusual URL structures.
Training users to ignore URLs entirely
Perhaps most concerning is how abstraction systems train users behaviorally. By emphasizing names over URLs, these systems encourage users to ignore the actual technical address of websites entirely. This creates a dangerous habit where users become accustomed to not checking URLs at all, the skill of URL parsing (which many users are already struggling with) atrophies further, and when users encounter links outside of the abstraction system (in emails, messages, etc.), they have even less ability to evaluate them. This behavioral conditioning could make users more vulnerable to phishing in contexts where the abstraction system isn't available.
Third-party dependency for security decisions
Epiarc and similar systems fundamentally shift security decisions from users to third parties. Instead of users evaluating URLs directly, they must trust the developers of the abstraction system, the curators of linkbases, and the integrity of the mapping process. This introduces multiple new points of potential failure and compromise. If any of these elements are breached, users have little ability to detect the problem since they're already trained to trust the system implicitly.
Why transparency may be the better approach for phishing prevention
Given the vulnerabilities created by abstraction systems, the transparent clean URL approach offers several significant advantages for phishing prevention:
Direct verification without intermediaries
Clean URLs allow users to directly verify the legitimacy of a website without trusting any intermediary. While users need education to parse URLs effectively, this skill empowers them rather than making them dependent on third parties.
Building upon existing infrastructure
The clean URL approach builds upon and improves the existing web infrastructure rather than creating an entirely new layer of abstraction. Modern browsers already implement features to highlight domains and show security indicators. These can be enhanced without introducing radical new dependencies.
Consistent security across contexts
URL-based security works consistently across all contexts — whether users are clicking links in emails, messages, documents, or applications. The abstraction approach only works within its own ecosystem, creating inconsistent security models across different user experiences.
Empowering users rather than dependency
Teaching users to understand URL basics and recognize phishing attempts empowers them with transferable skills. In contrast, abstraction systems create dependency on the system itself, potentially leaving users more vulnerable when operating outside its boundaries.
Avoiding new attack vectors
While clean URLs have their challenges, they don't introduce the new attack vectors that abstraction systems do, such as linkbase manipulation, context confusion, or third-party compromise.
The path forward: Improving URL readability without sacrificing security
Rather than hiding URLs behind abstraction, a more effective approach might be to improve how browsers present URLs to make them more understandable without sacrificing transparency. Several practical improvements could help:
Enhanced domain highlighting
Modern browsers already highlight the domain name, but this feature could be enhanced. Browsers could use stronger visual cues to separate the domain from the rest of the URL, implement different colors for top-level domains, subdomains, and paths, and provide more intuitive visual warnings for suspicious or unusual domain patterns.
Contextual security indicators
Browsers could provide more contextual information about websites without hiding the URL. This could include showing how long a domain has been registered, indicating whether this is a user's first visit to this domain, displaying reputation scores or previous user interactions with the site, and warning about recently registered domains (which are often used in phishing).
User education integrated into browsers
Rather than assuming users will never understand URLs, browsers could include subtle educational elements. These might include brief explanations of URL components when users hover over different parts of the address bar, progressive teaching of URL reading skills through subtle hints and tips, and gamification elements that reward users for correctly identifying suspicious URLs.
Organization-specific approaches
Organizations concerned about phishing could implement more targeted solutions. Financial institutions could register multiple common misspellings of their domains and redirect them to the legitimate site, companies could standardize on simpler, more memorable domains for critical services, and organizations could implement custom browser extensions for their employees that provide additional verification for company services.
Improved phishing detection without abstraction
Technologies for detecting and preventing phishing can be enhanced without hiding URLs. These improvements could include better browser-based phishing detection using machine learning, improved safe browsing databases with faster updates, email security gateways with more sophisticated URL analysis, and enhanced verification technologies like HTTPS certificates with extended validation.
Final Thoughts
While Epiarc and comparable abstraction methods strive to address the genuine issue of phishing, they may unintentionally create additional vulnerabilities. By concealing essential security information from users and introducing new dependencies and potential attack vectors, these systems might ultimately facilitate phishing instead of hindering it.
The clean URL approach, focused on transparency and education, offers a more robust path forward. By building upon the existing web infrastructure and empowering users with knowledge rather than hiding information from them, we can develop more effective phishing prevention strategies that don't introduce new security risks.
The most effective anti-phishing strategy likely lies not in abstracting away URLs entirely, but in making them more understandable while maintaining their visibility. By improving how browsers present URLs and helping users develop better URL reading skills, we can create a more secure web without sacrificing transparency or introducing new attack surfaces.